Secure Shell SSH Enabled FTP Adapter for BizTalk
Secure Shell (SSH) Enabled FTP Adapter for BizTalk
Since there is not enough information available on the sFTP adapters for BizTalk, thought would post this one, This document is more focused on the BizTalk side rather than SSH, however I have provided some basic background information on SSH servers and clients using the RSA key based authentication.
Requirement:
Transfer files to and from Secure Shell (SSH) Enabled servers, need to implement using sFTP protocol,
Explanation:
BizTalk 2004/2006 doesn’t have any built in support for sFTP adapters, they only support traditional FTP adapters, hence we are only left with two options, either we need to develop our own custom adapters for sFTP or purchase it from other clients,
I went ahead using the /n software SFTP Adapter, this lets you add sFTP adapter using the configuration settings, and transfer files remotely using sFTP, also has the feature to implement RSA Key based authentication using public and private keys, which I would be explaining later, http://www.nsoftware.com/products/biztalk/
Let me give you some background information for sFTP, where it is used, and how to implement it.
The /n software SFTP Adapter uses the SFTP protocol to transfer files to and from Secure Shell (SSH) Enabled servers. Using the adapter is identical to using the /n software FTPS Adapter, requiring only that you supply a server to connect to, user name, and password. As with the FTPS Adapter, simply bind your port to a BizTalk Orchestration and the SFTP Adapter will take care of the rest.
The SFTP Adapter features:
Installations:http://www.nsoftware.com/kb/tutorials/biztalksftpadapter.aspx#install
Get the sFTP adapter, go ahead with the installations, once installation is complete, you have to get the keys and activate it,
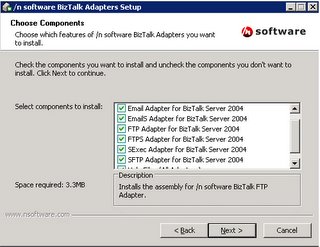
Once installation is done we need to register the adapter, which can be done using the BizTalk Administration Console,
sFTP configuration:
Process: RSA key based authentication
A more secure method of authentication is through the use of RSA keys. The basic principle is as follows. Each user generates a 1024bit public/private key pair,
Any host to which the user wants to connect must be aware of his public RSA key, as the server uses it during the authentication process. The user must place his public key living on the originating client machine, into his own authorized_keys file on the server.
When he wants to connect to that server, ssh will first negotiate an encrypted session, then send the server the client's public key. The server checks that the public key is in the user's authorized_keys. If so, the server sends the client a challenge (a random number encrypted with the user's public key). If the client can then send back the random number unencrypted, it has just proven that it has the private key (there is no other way to unencrypt the challenge number), and is therefore authentic.
The user's private key is a very sensitive piece of data - with it, anyone can connect to any host on which the corresponding public key is in the authorized_keys. Therefore, the user's private key is never written to disk unencrypted.
Public key authentication solves this problem. You generate a key pair, consisting of a public key (which everybody is allowed to know) and a private key (which you keep secret and do not give to anybody). The private key is able to generate signatures. A signature created using your private key cannot be forged by anybody who does not have that key; but anybody who has your public key can verify that a particular signature is genuine.
The Authentication layer uses one or more of the following authentication methods to validate the user:
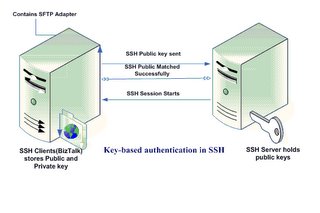
Summary of the steps;
Key-based authentication in a SSH environment uses public and private keys. The following is a summary of the steps required to generate a key pair for SSH:
Here I have provided both types of authentication,
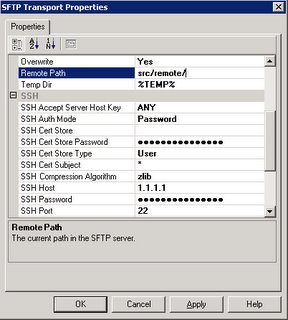
This is based on the RSA key based authentication:
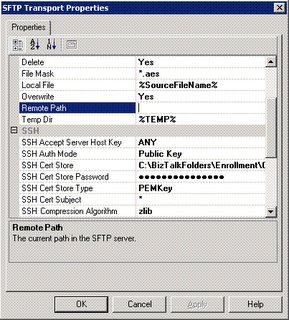
sFTP Adapter properties(nSoftware):
AddressURI:
Since there is not enough information available on the sFTP adapters for BizTalk, thought would post this one, This document is more focused on the BizTalk side rather than SSH, however I have provided some basic background information on SSH servers and clients using the RSA key based authentication.
Requirement:
Transfer files to and from Secure Shell (SSH) Enabled servers, need to implement using sFTP protocol,
Explanation:
BizTalk 2004/2006 doesn’t have any built in support for sFTP adapters, they only support traditional FTP adapters, hence we are only left with two options, either we need to develop our own custom adapters for sFTP or purchase it from other clients,
I went ahead using the /n software SFTP Adapter, this lets you add sFTP adapter using the configuration settings, and transfer files remotely using sFTP, also has the feature to implement RSA Key based authentication using public and private keys, which I would be explaining later, http://www.nsoftware.com/products/biztalk/
Let me give you some background information for sFTP, where it is used, and how to implement it.
The /n software SFTP Adapter uses the SFTP protocol to transfer files to and from Secure Shell (SSH) Enabled servers. Using the adapter is identical to using the /n software FTPS Adapter, requiring only that you supply a server to connect to, user name, and password. As with the FTPS Adapter, simply bind your port to a BizTalk Orchestration and the SFTP Adapter will take care of the rest.
The SFTP Adapter features:
- Send and receive files to/from BizTalk Adapters and any FTP or Secure Shell (SSH) Enabled FTP server
- Secure Shell (SSH) data protection
- Secure Shell (SSH) - a low-level communications protocol providing security via strong encryption and advanced cryptography.
- Secure Shell Public-Key Authentication ( RSA Key )
Installations:http://www.nsoftware.com/kb/tutorials/biztalksftpadapter.aspx#install
Get the sFTP adapter, go ahead with the installations, once installation is complete, you have to get the keys and activate it,

Once installation is done we need to register the adapter, which can be done using the BizTalk Administration Console,
sFTP configuration:

Process: RSA key based authentication
A more secure method of authentication is through the use of RSA keys. The basic principle is as follows. Each user generates a 1024bit public/private key pair,
Any host to which the user wants to connect must be aware of his public RSA key, as the server uses it during the authentication process. The user must place his public key living on the originating client machine, into his own authorized_keys file on the server.
When he wants to connect to that server, ssh will first negotiate an encrypted session, then send the server the client's public key. The server checks that the public key is in the user's authorized_keys. If so, the server sends the client a challenge (a random number encrypted with the user's public key). If the client can then send back the random number unencrypted, it has just proven that it has the private key (there is no other way to unencrypt the challenge number), and is therefore authentic.
The user's private key is a very sensitive piece of data - with it, anyone can connect to any host on which the corresponding public key is in the authorized_keys. Therefore, the user's private key is never written to disk unencrypted.
Public key authentication solves this problem. You generate a key pair, consisting of a public key (which everybody is allowed to know) and a private key (which you keep secret and do not give to anybody). The private key is able to generate signatures. A signature created using your private key cannot be forged by anybody who does not have that key; but anybody who has your public key can verify that a particular signature is genuine.
The Authentication layer uses one or more of the following authentication methods to validate the user:
- Password Authentication
- RSA/DSA Public-Key Authentication
- Kerberos Authentication
- Host-based Client Authentication

Summary of the steps;
Key-based authentication in a SSH environment uses public and private keys. The following is a summary of the steps required to generate a key pair for SSH:
- An authorized user must generate a public and private key pair.
- The user has the option of password protecting the private key (RSA key), which is recommended in almost all environments.
- The user's public key needs to be securely uploaded to the SSH server, usually stored in the user's home directory. For example, the user Vamsi would have a public key stored in /home/Vamsi/.ssh/ or Documents and Settings\Vamsi\.ssh of the SSH server.
- Authorization, Identification, and authorized_keys files need to be populated.
- Public-key authentication needs to be configured on the SSH server, which is enabled by default on many SSH installations.
- First, install the SFTP adapter.
- Then create the send and/or receive ports as needed based on sFTP configuration.
- Once done, assuming that we gotten this far. Let’s say that we have set up a Receive location that will pick up files from some remote SFTP server - so we have to setup a Receive location of transport type /n software SFTP.
- From the BizTalk Explorer, edit your receive location. In the Address (URI) configuration property, click on the ellipsis (...). This will bring up properties specific for the adapter. This is will let us configure the actual SFTP transport properties. Included here are properties to specify the sftp server, port, user, etc.
- Now, lets say the client has given us an RSA (private) key for authentication to this SFTP server where we will pick up files. This means we want to set the "SSH Auth Mode" property to "Public Key" (as opposed to password authentication). This tells the adapter to authenticate to the server using a username and RSA key (private) rather than a username and password. Specify the username of course in the "SSH User" property. We can leave the "SSH Password" property blank in the case of public key based authentication.
- Now that we've told the adapter to use public key auth, we must point it to the private key to use. I have used RSA key, (Note: If we need we can also go with a PFX file, or a PEM file, we can install the key to a machine store and access it from there as well, depending on the client needs).
- Anyway lets come back to the way I have implemented, I went with RSA key based authentication, hence I had to provide the SSH Cert Store with location of the rsa key(id_rsa), for the adapter to pick it up,
- Once this is done, we need to specify what type of SSHCertStore it is, Typically the public key might be in a PEM file, in which case you'd set the "SSH Cert Store Type" property to "PEMKey".
- Finally set the "SSH Cert Subject" to "*", which means the first certificate or key in the store.
- That’s it, we should be able to capture the file from the remote location,
Here I have provided both types of authentication,
- Password based authentication
- RSA key based authentication

This is based on the RSA key based authentication:

sFTP Adapter properties(nSoftware):
AddressURI:
- Remote File: %SourceFileName%
- Remote Path: “/usr/Path/”
- SSH Accept Server Host Key: ALL
- SSH Auth Mode: Public Key
- SSH Cert Store: “home\RSAKey\SFTP_DEV\id_rsa”
- SSH Cert Store Password: <Empty>
- SSH Cert Store Type: PEMKey
- SSHCert Subject: "*"
- SSHHost: <IPAddress>
- SSHPassword: <empty>
- SSHPort: 22
- SSHUser: <user>

<< Home